Expected changes in IT/OT convergence and industrial security
Ten
years ago, I was brought into the industrial security arena by a top
company executive in who was convinced that we needed traditional
endpoint protection on smart meters.
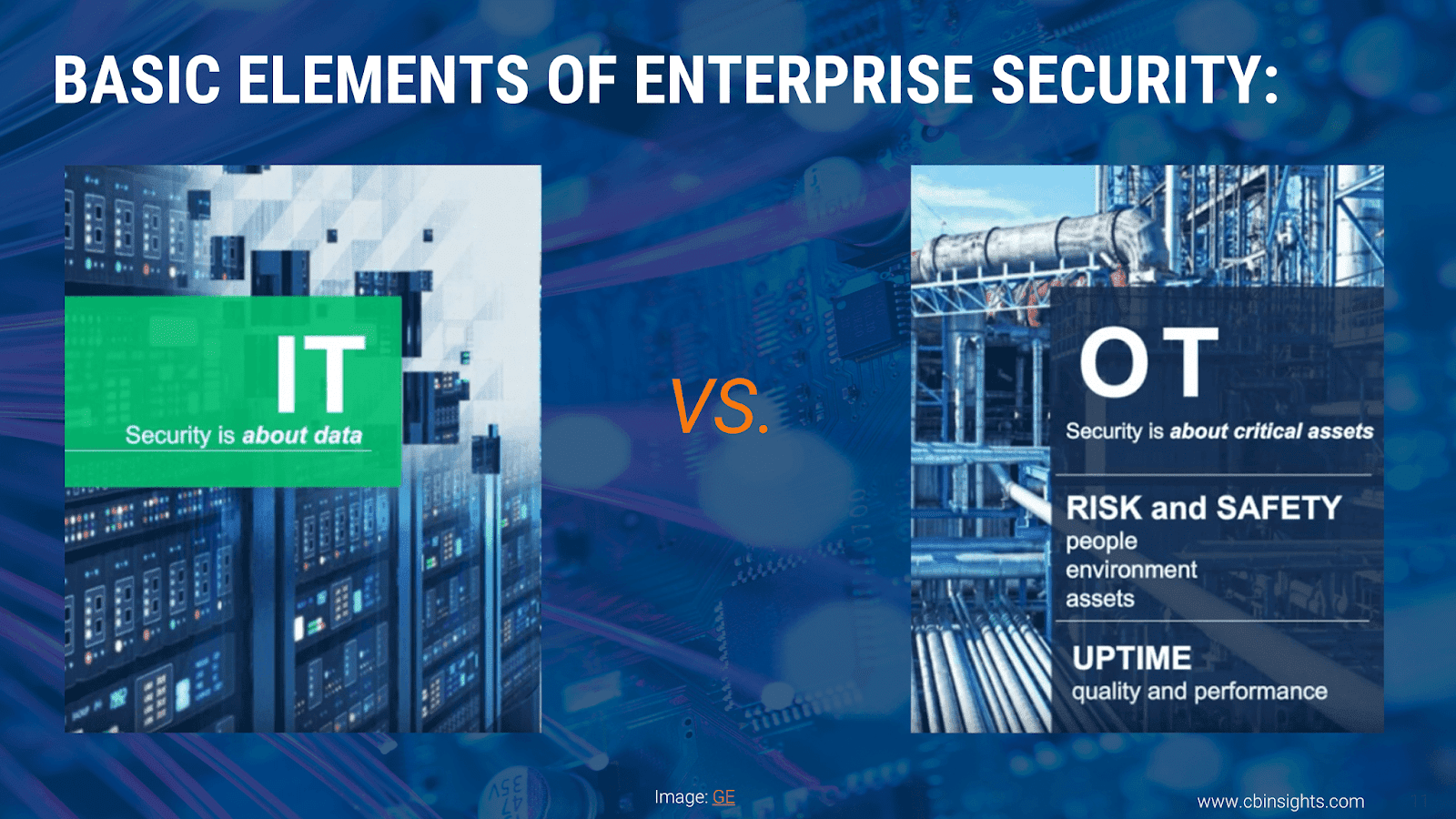
I had spent fifteen years before that in enterprise security, so it
took a while to shape my focus around the nature of the problem of IT/OT
convergence and industrial security.
I have had the pleasure of being on both sides of the fence – from a
major IT security provider building major partnerships with automation
vendors, to specifically working at an automation networking company
developing a major security practice. I’m a firm believer that we can
have a world with basic security hygiene across all verticals within critical infrastructure.
Over the past year, we have seen a continued cross-pollination: IT
security staff trying to step on the plant floor and plant teams trying
to understand IT security. At an oil and gas security conference I
attended last fall, a full 40 percent of the people were from the OT
side, and a full 50 percent of those people were involved in running the
operations of a plant.
This shift means that IT security has become imperative for ICS
environments, and that we can expect a lot of change. Here are four
areas in which I believe we’ll see most of it:
Unified visibility, detection and response across industrial environments
Over the past few years, we have witnessed the second wave of
industrial security companies advancing visibility in industrial
environments above the traditional detective controls of patching,
endpoint security and so forth.
Pressured by the Board, CISOs and CIOs are rushing to deploy
SOMETHING to provide visibility, while pushing their plan to “do no
harm” to operational environments and avoiding impacting production. We
will see more industry testing of these approaches, further validation
of claims from these solution providers, and companies sharing their
success stories about large global deployments.
One of the key issues to monitor is how a company sets up its IT security operations center
(SOC) and process control network (PCN) teams to rapidly collect
information from the plants, visualize the traffic, and provide
meaningful analysis back to the plant operators.
Increased intentional and unintentional attacks impacting ICS
We started out 2018 with Trisis/Triton, which demonstrated the
unintentional exploit of a safety system. Last year WannaCry exposed one
of the core problems in industrial environments – legacy unpatched
servers – with a full-fledged ransomware attack. CrashOverride showed
how a sophisticated attacker can build a modular malware framework for
substation environments, to thoroughly disrupt an industrial process by
exploiting the critical industrial protocols used between the control
and operational functions of a plant.
Despite our heightened awareness, this combination of sophistication,
exposure of basic defenses, and reliance on security by obscurity will
continue throughout 2018.
Security offerings and support of security solutions will continue to increase
Since Stuxnet, automation vendors have struggled to fix their product
vulnerabilities. They provide their customers a security offering which
will protect not just their systems, but also protect a heterogeneous
plant environment. IIoT Services like GE Predix and Siemens MindSphere,
which are based on cloud-connected data-driven services, further
compound this issue. End users are trying to rely on manufacturers to
provide security controls or some level of testing and assurance that
their security solutions will not impact plant uptime.
In 2018, I see automation vendors combining security service
offerings with cloud offerings to help address these issues.
Furthermore, due to customer demand for network visibility, some
forward-thinking vendors will provide visibility into their networks and
configurations to better allow security tools to monitor their
environments properly.
The need for an IT/OT security specific skill set will become a significant issue
The cybersecurity industry is projected to reach 1.8 million unfilled
roles by 2020. The added complexities of a converged IT/OT security
environment could amplify perceived barriers to entry, as organizations
struggle to manage the aging workforce of their plant teams with the
Millennial generation of new cybersecurity talent.
The industry will be forced to find solutions for tapping talent by
leveraging technologies that make it possible to attract, upskill and
retain the next generation of security staff. One approach is to
introduce highly immersive tools including 4-D imagery, virtual reality,
and augmented or mixed reality – much like the environments in which
the Minecraft generation grew up. The good news is that the ICS industry
already uses immersive data visualization to discover oil in the
subsurface, so adoption on the security side of the house is not
far-fetched.
Organizations who leverage their talent pool and industry education
to build security leaders of tomorrow will be in a good position to
address the problem.


Good information. I really appreciate your post. I found information on best OT Security platform. Thanks for sharing
ReplyDelete